Broccoli (Bounce Finance) is a cryptocurrency token with no connection to Bounce Finance. It's a high-risk meme coin with a market cap under $120k and a 99.76% drop from its peak. Experts warn it lacks utility, transparency, and exchange listings. Current data shows minimal trading activity and potential rug pull risks. Avoid investing in this token.
Author: Julia Icone - Page 2
A 51% attack lets malicious actors reverse transactions by controlling more than half of a blockchain's mining power. While Bitcoin is safe, smaller cryptocurrencies like Ethereum Classic have been hit. Learn how it works, why it matters, and how to stay protected.
Australia requires all crypto exchanges trading fiat for digital currency to register with AUSTRAC. As of March 2026, the rules expand to cover crypto-to-crypto trading and custody services. Know the requirements, avoid penalties, and stay compliant.
There is no Hyperion crypto exchange. Scammers are using the name to trick users into depositing funds. Learn what Hyperion.fund, Hyperion Token, and Hyperion Networks actually do - and how to avoid losing money to fake crypto platforms.
Uniswap v3 is the leading decentralized exchange with concentrated liquidity, lower fees on L2s, and deep trading volume. It’s powerful but complex-perfect for experienced users who want full control over their crypto trades.
zk-SNARKs and zk-STARKs are two zero-knowledge proof systems that enable private, scalable blockchain transactions. Learn how they differ in security, cost, speed, and future-proofing to choose the right one for your project.
NDAX is Canada's top crypto exchange for trading Bitcoin, Ethereum, and 37+ other coins directly with Canadian dollars. Low fees, strong security, and 24/7 support make it the best choice for Canadian investors.
Russia doesn't ban all crypto exchanges - it forces them to choose between compliance and closure. Garantex and Grinex were shut down for sanctions evasion, while Binance and Kraken are blocked by infrastructure. Only state-approved platforms survive.
GOBL (GOBL) is a high-risk meme coin with no team, no utility, and near-zero liquidity. Learn its price, where to buy it, why experts warn against it, and whether it's worth your money in 2026.
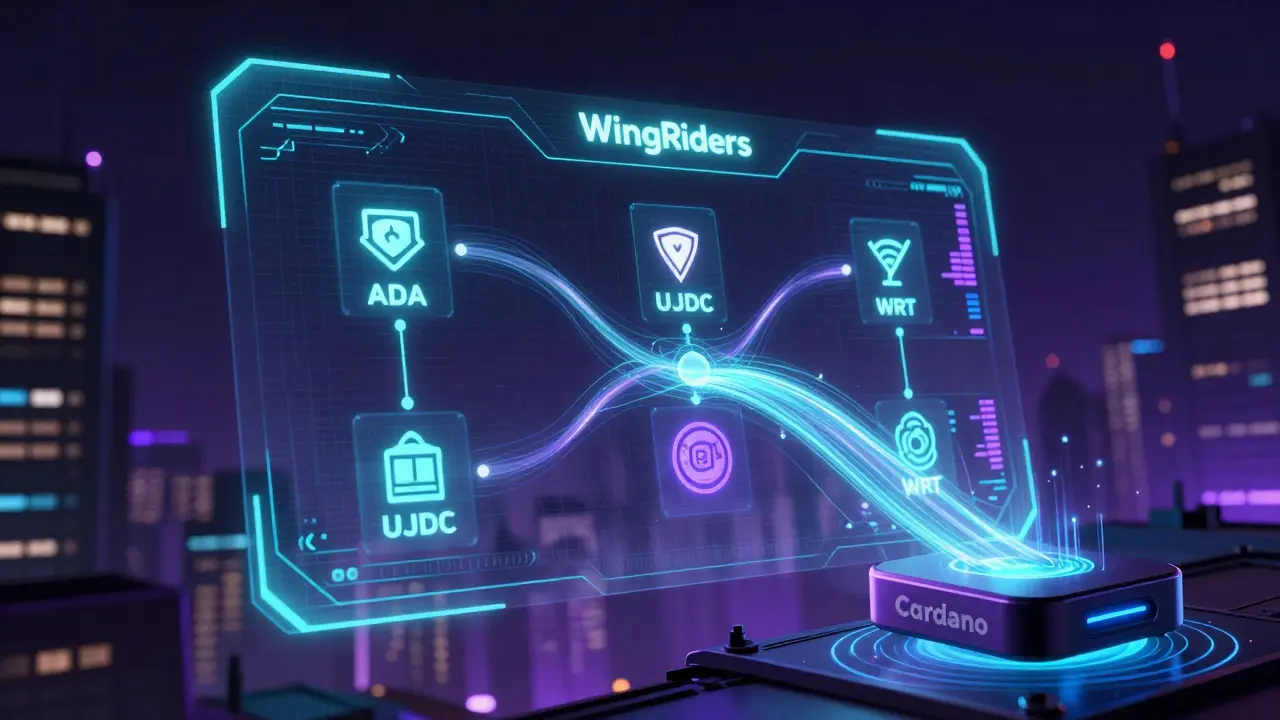
WingRiders is Cardano's leading decentralized exchange with stablecoin swaps, multi-reward farming, and DAO governance. Learn how it works, its WRT token, and why it's still the best DeFi option on Cardano in 2026.
Learn how to protect your crypto from phishing in 2026 with proven steps: hardware wallets, seed phrase safety, MFA, password managers, and training your brain to spot scams before it's too late.
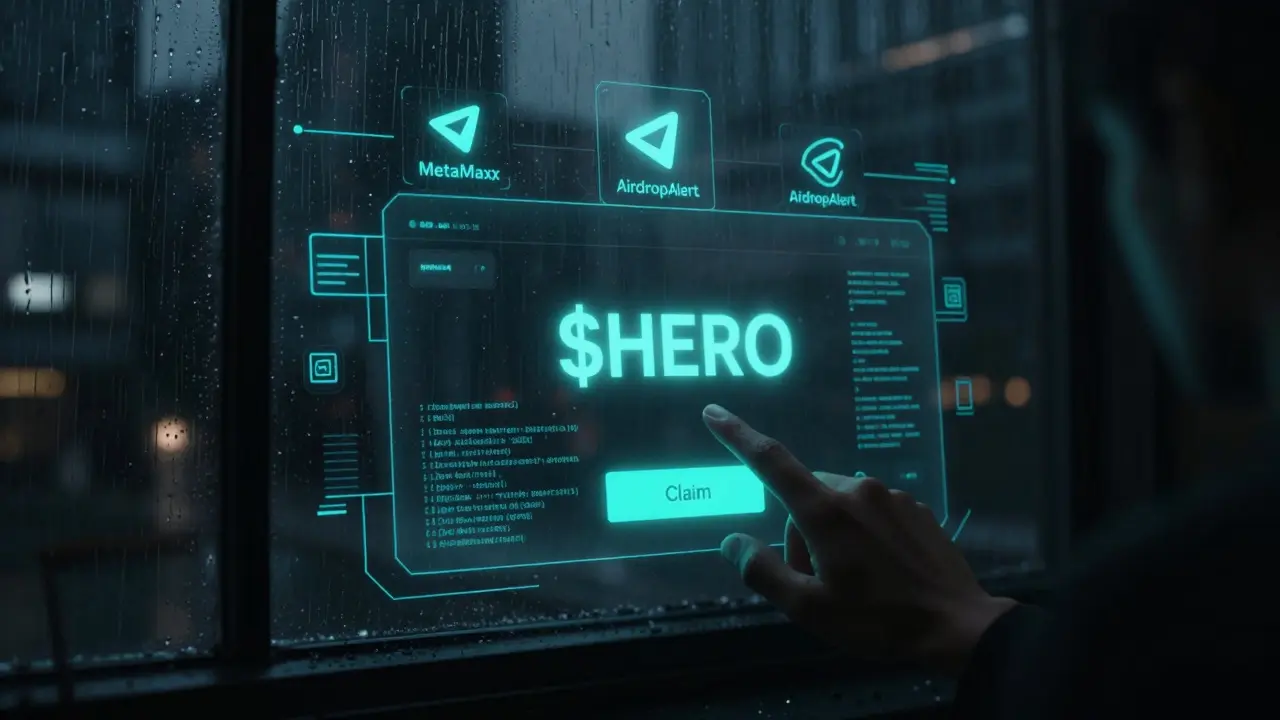
The Step Hero airdrop offers $HERO tokens with a $4,800 prize pool, but official details are scarce. Learn how to check eligibility, avoid scams, and safely participate in this quiet but active 2026 crypto airdrop.